Establishing a robust firewall configuration within Plesk is fundamental for safeguarding servers against potential cyber threats and unwanted network traffic. The integrated firewall solution, seamlessly accessible through the Plesk control panel, offers precise control over network access, effectively mitigating security vulnerabilities and enhancing overall system integrity.
Key Security Considerations
- Strategic Rule Implementation: Properly configured firewall rules are essential for preventing unauthorized external access to your server resources.
- Seamless Plesk Integration: The firewall's deep integration within the Plesk control panel ensures straightforward and intuitive management, streamlining security operations.
- Robust Default Configurations: Predefined security settings provide a strong defensive posture right from the initial server setup, offering immediate protection.
- Comprehensive Logging and Monitoring: Detailed logs and continuous monitoring capabilities allow for the tracking and analysis of attempted attacks, providing crucial insights into security events.
- Enhanced Protection with Extensions: Utilizing extensions like Fail2Ban significantly bolsters defense mechanisms against persistent brute-force attacks, adding an extra layer of security.
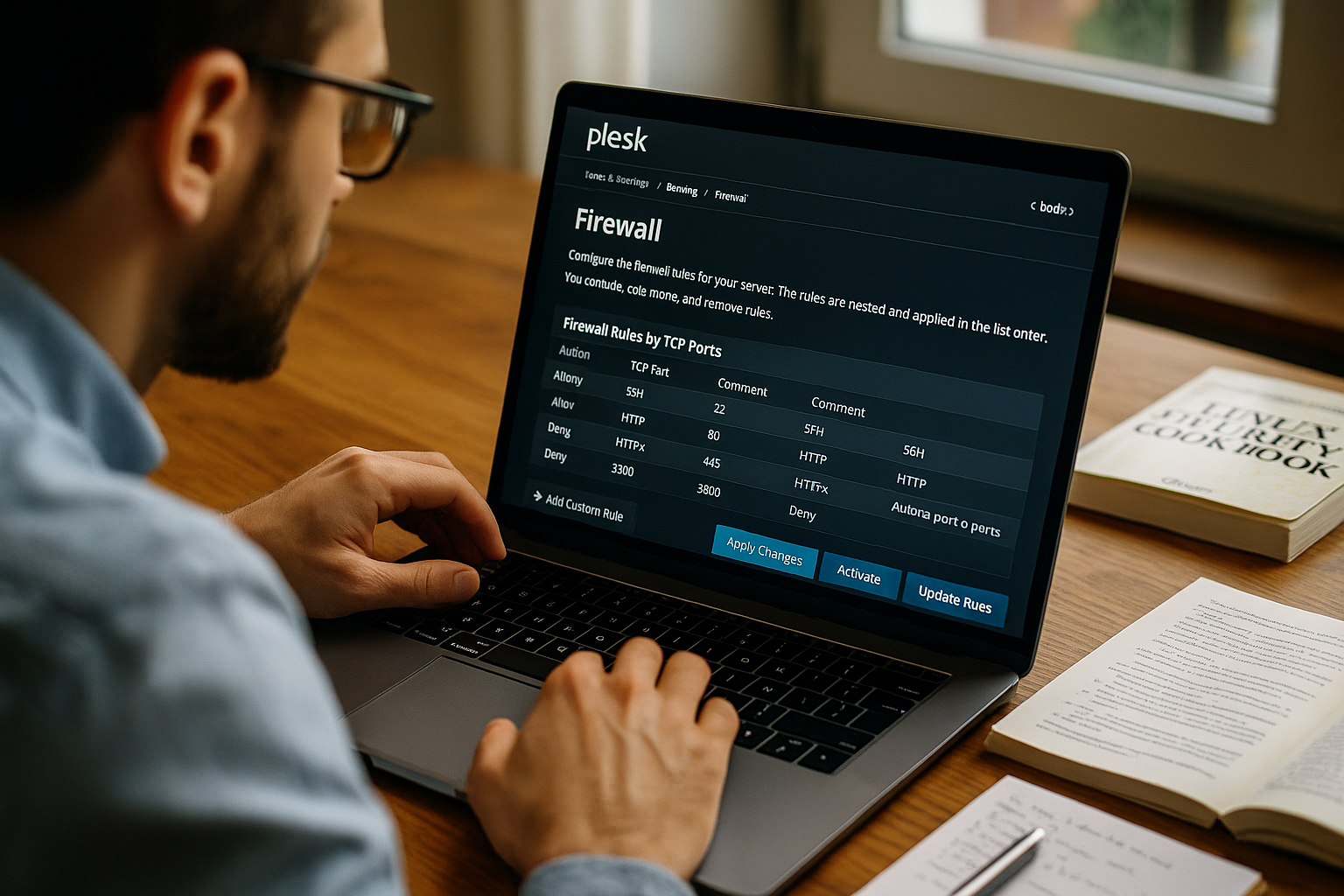
Understanding the Plesk Firewall's Capabilities
The Plesk firewall stands out as a robust, fully integrated security component within the hosting control panel, eliminating the need for separate software installations. It operates by meticulously filtering network data based on user-defined rules, thereby safeguarding critical services such as HTTP, HTTPS, FTP, and SSH from unauthorized intrusions. A key strength lies in its intuitive graphical user interface (GUI), which simplifies the process of modifying security settings, making it accessible even for those new to server administration. For more experienced users requiring granular control, comprehensive manual configuration options are readily available for crafting sophisticated rules. This potent combination of an approachable interface and precise traffic management capabilities makes the Plesk firewall a highly effective tool for server security.
Step-by-Step Configuration of the Plesk Firewall
Administering the firewall is a straightforward process, managed directly from your Plesk dashboard. Navigate to the "Tools & Settings" section, and then select "Firewall." Once activated, you gain the ability to precisely define whether individual applications or specific network ports should be open or blocked. Both incoming and outgoing data traffic can be regulated independently; for instance, you might choose to restrict access to a particular service only to a set of predefined IP addresses. It is important to remember that after making any changes, the firewall service must be restarted for the new rules to become active. The user interface provides real-time visibility, clearly indicating which ports are currently open or blocked, offering immediate feedback on your security posture.

Recommended Firewall Rules for Common Services
For optimal server protection, it is a critical security practice to keep only the absolutely essential ports open on your firewall. Overly permissive rules can significantly increase your server's attack surface. The table below outlines recommended firewall settings tailored for common web hosting environments, balancing accessibility with robust security:
| Service | Port | Status |
|---|---|---|
| SSH (Secure Shell for remote access) | 22 (TCP) | Open – Strictly limited to administrator IP addresses to prevent unauthorized remote access. |
| HTTP (Standard web traffic) | 80 (TCP) | Open – Accessible for all IP addresses to ensure public website availability. |
| HTTPS (Secure web traffic with SSL/TLS) | 443 (TCP) | Open – Accessible for all IP addresses to facilitate secure website communication. |
| FTP (File Transfer Protocol) | 21 (TCP) + passive ports | Blocked – Recommended to keep closed if not actively used. Consider SFTP or SCP for secure file transfers. |
| MySQL remote access | 3306 (TCP) | Blocked – Only open for specific, trusted IP addresses if remote database access is absolutely necessary. |
Enhancing Protection with Fail2Ban
Integrating the Plesk firewall with the Fail2Ban service creates a powerful, multi-layered defense against persistent login attempts and automated attacks. Fail2Ban operates by continuously monitoring server log files for suspicious activities, such as an excessive number of failed login attempts within a defined period. Upon detecting such patterns, it automatically blocks the originating IP address, effectively preventing further malicious access. This measure is particularly effective for services like SSH, where it significantly bolsters defenses against relentless brute-force attacks, thereby enhancing overall server security.

Efficient Firewall Administration Techniques
A significant benefit of the Plesk firewall is its streamlined administration, largely facilitated by preconfigured security profiles. These profiles enable the activation of essential ports for common services such as web servers, mail servers, or FTP with just a single click, simplifying initial setup. For users requiring more tailored solutions, these profiles can be customized, or entirely new templates can be created to meet specific security requirements. For routine and recurring changes, leveraging scripting or Command Line Interface (CLI) commands through firewalld (on Linux systems) offers a highly efficient approach. Furthermore, for comprehensive oversight, external monitoring solutions can be integrated, utilizing protocols like SNMP or advanced central log evaluation tools to maintain a clear picture of firewall activity and server health.
Permanently Addressing Security Gaps
While a robust firewall is indispensable, its effectiveness is diminished if unnecessary services or ports remain open. It is therefore crucial to conduct regular audits to verify that all open ports are genuinely required for operational purposes. A common vulnerability often overlooked is the continued use of standard FTP access, which can frequently be replaced by more secure alternatives like SFTP (SSH File Transfer Protocol). Similarly, remote access to MySQL databases should be strictly limited, allowing connections only from specific, authorized IP addresses. A highly effective firewall configuration adheres to the "default deny" principle, meaning it permits as little outgoing traffic as possible by default, thus minimizing potential attack vectors from within the server. Embracing these proactive measures can significantly fortify your server's security posture.

Understanding and Evaluating Firewall Protocols
The Plesk firewall meticulously records various network events, including blocked connections, successful packet accesses, and erroneous requests. This detailed logging is invaluable, providing critical forensic evidence and insights in the event of security incidents or attempted breaches. By regularly reviewing these log files, administrators can identify recurring attack patterns, pinpoint common sources of malicious activity, and implement more targeted countermeasures, particularly against frequently blocked IP addresses. Automated reporting tools such as Logwatch or Fail2Ban-Reporter can streamline this process, generating concise summaries of firewall activity. Furthermore, configuring notification plugins to send immediate alerts via email or other channels ensures that administrators are promptly informed of any unusual or suspicious behavior, allowing for a rapid response.
Structuring Access Management for Teams
In team environments, implementing a well-structured access management strategy within Plesk is paramount for maintaining server security. Plesk facilitates the creation of users with varying levels of authorization, ensuring that direct access to sensitive firewall configurations is restricted to only essential personnel. For larger teams, clearly defining and assigning roles and permissions is highly recommended. This approach minimizes the risk of accidental configuration changes and safeguards critical security settings. When collaborating with external service providers, it is best practice to explicitly whitelist their specific IP addresses for the duration of their engagement and promptly remove these permissions once the project is concluded. This disciplined method ensures robust control and a clear overview of who has access to which parts of your server infrastructure.
Advanced Firewall Concepts for Enhanced Security
Beyond the fundamental functionalities, the firewall configuration within Plesk offers avenues for incorporating advanced security mechanisms. A key concept here is the strategic implementation of "outbound" rules. While inbound connections typically receive significant attention, it's crucial not to overlook the threat posed by unauthorized outgoing traffic. Malicious software, for instance, might attempt to send sensitive data from your server to external entities. Outbound rules can effectively prevent such scenarios by restricting what information can leave your server.
Another vital consideration in modern network security is the proper handling of IPv6. Many legacy firewall configurations primarily focus on IPv4, despite IPv6 being an increasingly prevalent internet protocol. Plesk allows for the parallel definition of IPv6 rules alongside your existing IPv4 rules. It is absolutely critical to avoid broad "allow any" configurations for IPv6, as this can inadvertently create significant security vulnerabilities. Activating IPv6 should ideally coincide with a fully configured and secure server environment, encompassing DNS and network infrastructure, to ensure that security settings are consistently applied across both protocol versions. Neglecting IPv6 in your firewall strategy can lead to unforeseen gaps, as malicious traffic may bypass IPv4-focused defenses.
For highly sophisticated deployments, administrators might explore moving specific services to isolated IP address spaces or implementing Virtual Local Area Network (VLAN) structures. These advanced network segmentation techniques enable exceptionally granular control over access within the data center environment. While VLANs and dedicated IP ranges are not directly provisioned as one-click solutions within Plesk, they can be established at the operating system level and subsequently integrated with the Plesk firewall rules. This approach allows, for example, a critical database server to reside in a highly protected segment, minimizing its external accessibility and enhancing its security posture.
Implementing DMZ and Port Forwarding in Plesk
For specific security architectures, isolating individual services or entire systems within a Demilitarized Zone (DMZ) can be highly beneficial. This strategy is particularly relevant for applications that need to be publicly accessible but must be prevented from having direct access to internal, more sensitive network resources. Typically, a DMZ is established using distinct firewall zones. While Plesk doesn't offer a direct one-click DMZ solution, the necessary firewall rules can be configured by combining settings at the host operating system level with the intuitive Plesk interface. This method allows incoming packets to be precisely forwarded to DMZ resources without exposing the entire internal network.
Traditional port forwarding is another important consideration. If you are hosting local services on non-standard ports or utilizing complex software requiring specific external access, the Plesk firewall allows you to forward certain ports to the outside world. However, these port forwarding rules should be implemented with extreme caution and configured as restrictively as possible. For critical administration ports (e.g., 8080 for web interfaces), using a Virtual Private Network (VPN) tunnel is often a far more secure alternative than making them publicly accessible. A VPN encrypts all traffic and provides a secure conduit into your network, dramatically reducing the external attack surface and protecting sensitive administrative access.
Leveraging Log Management for Forensic Analysis
To achieve a truly comprehensive security posture, structured log management is an indispensable practice. Beyond the firewall's own records, various server components—such as web servers, mail servers, and other critical services—generate extensive log data detailing access attempts and system events. Consolidating all this log information, for instance, via a centralized syslog server, is crucial for effective forensic analysis in the event of a security incident. Best practices include regularly rotating, compressing, and archiving logs to maintain manageable storage and ensure data integrity. Tools like Logstash or Graylog are invaluable for efficiently filtering, analyzing, and visualizing large volumes of log data, making patterns and anomalies easier to spot. Furthermore, safeguarding logs against manipulation is paramount; storing them on a separate, hardened server is an effective method to ensure their trustworthiness for auditing and forensic purposes.
The Plesk firewall's logs offer particularly insightful data. They meticulously record which IP addresses are repeatedly blocked, which ports are frequently scanned in a suspicious manner, and how often connection attempts are made on ports that are intentionally closed. Recognizing these recurring patterns is often a strong indicator of automated attack attempts or reconnaissance efforts. If specific IP ranges consistently exhibit suspicious behavior, a proactive measure might involve temporarily or permanently blocking entire network segments, provided there is no legitimate business requirement for access from those regions. This strategic use of log data transforms raw information into actionable security intelligence.
Troubleshooting Common Configuration Problems
In practical server administration, it is not uncommon to encounter scenarios where firewall configurations lead to unintended blocking or allowing of traffic. A classic example is inadvertently closing a port that a critical service relies upon, rendering an application inaccessible. In such situations, a systematic troubleshooting approach is beneficial: consider deactivating the Plesk firewall incrementally or removing individual rules one by one to isolate the root cause of the issue. The system logs, typically found at /var/log/messages or /var/log/firewalld on Linux systems, are also invaluable resources for identifying specific error messages related to firewall operations.
Should a more severe issue arise, such as being locked out of the Plesk Control Panel due to an inadvertently blocked internal port, direct access via the host system or an emergency SSH login (often through a KVM console provided by the hosting provider) becomes necessary. From this low-level access, the underlying firewall services (e.g., firewalld or iptables) can be manually stopped or reset. This allows you to correct the erroneous configuration and restore normal operation. Crucially, it is always advisable to thoroughly document your original firewall settings before making any significant changes. This documentation serves as a vital reference point, enabling you to precisely track and revert any problematic modifications, ensuring a smooth recovery process.
Application Example: Securing Your Email Server
Securing an email server presents a distinct set of challenges, as it relies on several publicly exposed ports for sending and receiving messages, including 25 (SMTP), 110 (POP3), and 143 (IMAP). These ports, due to their essential nature, are frequently targeted by malicious actors. To establish a robust defense, it is strongly recommended to enforce SMTP authentication for all outgoing mail and secure all connections using Transport Layer Security (TLS) encryption. Furthermore, access to any webmail interfaces should be exclusively via HTTPS to protect login credentials and data in transit. By combining these practices with mail server-specific firewall rules, administrators can achieve a significantly higher level of protection, effectively mitigating spam and defending against authentication-based attacks.
Automating Firewall Backups and Restoration
In the dynamic environment of server management, misconfigurations can occasionally occur. In such events, having a recent backup of your firewall settings can be an invaluable lifeline, enabling swift recovery. Plesk provides a convenient feature to export and archive all configured firewall rules. These backups can then be easily restored in an emergency, minimizing downtime and mitigating potential security risks. For managing larger infrastructures, implementing an automated weekly backup schedule via the Command Line Interface (CLI) or a cron job is a highly recommended practice. Regularly reviewing the administration panel for firewall rules further enhances transparency, allowing administrators to stay informed about their security configurations and make timely adjustments.
Final Thoughts: Firewall Management as a Security Routine
Effective firewall management within Plesk should be viewed not as a singular event, but as an essential, continuous security routine. It is highly advisable to conduct a comprehensive security review on a monthly basis, diligently examining all open ports and services, and promptly removing any unnecessary exceptions. The synergistic combination of a robust firewall, proactive tools like Fail2Ban, and meticulously managed user rights not only provides formidable protection against diverse attacks but also instills confidence in your daily hosting operations. Administrators who consistently evaluate log data and automate system reports ensure they remain perpetually informed about their server's security status. Ultimately, a Plesk firewall, much like a physical door lock, requires regular engagement: secure it diligently, inspect it routinely, and promptly address any deficiencies to maintain an impenetrable defense.




