In today\'s digital landscape, relying solely on passwords for account security is no longer sufficient. Weak passwords are highly susceptible to sophisticated threats like brute-force attacks, and even robust passwords can be compromised. To significantly bolster the security of your Plesk account, it is strongly recommended to implement Multi-Factor Authentication (MFA).
MFA introduces an essential second layer of security to your Plesk login process. While passwords serve as the initial defense, MFA adds an additional verification step. Currently, this second security layer typically involves one-time passwords, often referred to as verification codes, which are dynamically generated by a dedicated MFA application on your smartphone. Throughout this guide, we will use the term "verification codes" to refer to these one-time passwords.
Setting Up Multi-Factor Authentication (MFA) in Plesk
Configuring Multi-Factor Authentication for your Plesk account is a straightforward process that significantly enhances your login security. Follow these steps to enable login with verification codes:
Begin by installing a trusted Multi-Factor Authentication (MFA) application on your smartphone. Popular choices include Google Authenticator, Microsoft Authenticator, or any other compatible MFA app you prefer.
Navigate to your Plesk interface and click on My Profile. Scroll down until you locate the "Multi-Factor Authentication (MFA)" section, then click on the provided link to proceed with the setup.
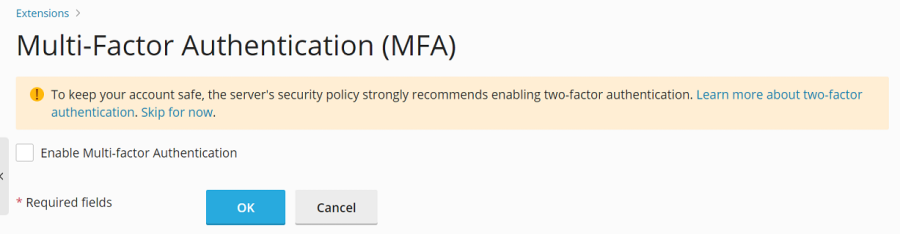
On the MFA setup page, mark the checkbox labeled "Enable Multi-factor Authentication" to activate the feature.
Using your smartphone\'s MFA app, scan the unique QR code displayed on your screen. Upon successful scanning, your authentication app will display the hostname of your Plesk server. For instance, the Google Authenticator app will show a 6-digit verification code directly beneath the hostname. Other MFA applications might require you to tap the hostname to reveal the code.
Input the 6-digit verification code from your MFA app into the designated field in the Plesk interface.
For added convenience, if you wish to bypass entering a verification code during subsequent logins from a specific device, select the "Enable the \'Remember Device\' feature" checkbox. Important Warning: Only enable the "Remember Device" feature on your personal, trusted devices. Activating this feature on a shared or public device could potentially allow unauthorized third parties to gain access to your Plesk account.
When the "Remember Device" feature is active, your device will be recognized for a predetermined number of days, eliminating the need to enter a verification code for each login during that period. Once this duration expires, or if your browser\'s cache is cleared, you will be prompted to enter a verification code again to verify your identity.
Even with the "Remember Device" feature enabled, if you log in to Plesk from a new or unrecognized device, you will still be prompted to provide a verification code. On such occasions, you will also notice a checkbox stating "Remember this device for n days," where \'n\' corresponds to the number of days you previously configured. To ensure this "Remember Device" checkbox is automatically selected by default whenever you access Plesk from a new device, check the "Preselect the \'Remember Device\' checkbox" option.
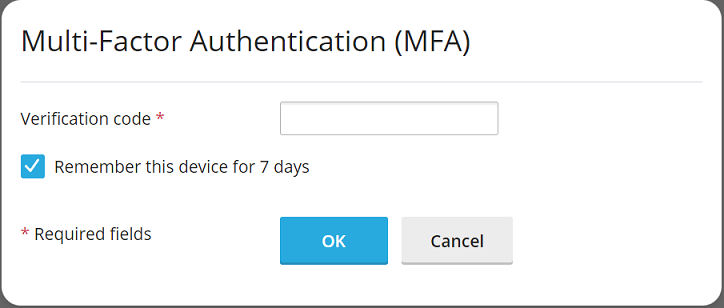
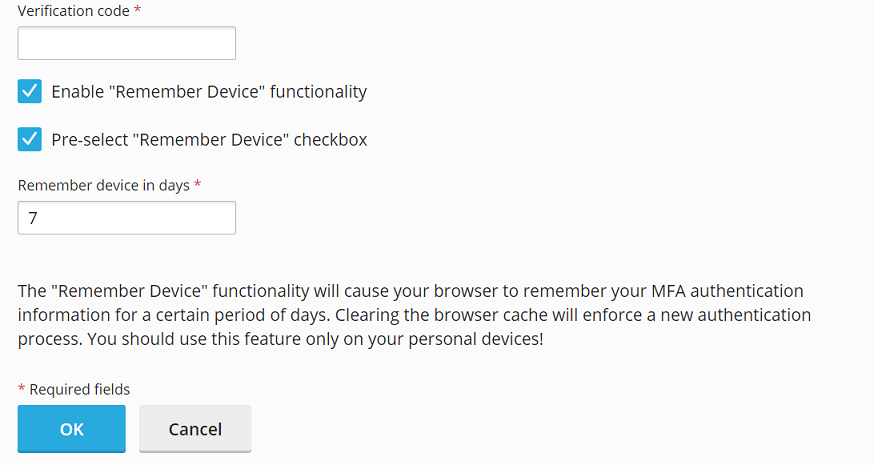
To finalize the setup and apply your settings, click OK.
Congratulations! You have successfully configured Multi-Factor Authentication for your Plesk account. From this point forward, each time you attempt to log in to Plesk, you will be prompted to enter a verification code generated by your chosen MFA application, adding a critical layer of protection to your account.
Enforcing Multi-Factor Authentication Usage in Plesk
Plesk facilitates Multi-Factor Authentication through its dedicated Multi-Factor Authentication (MFA) extension, which is included by default within the recommended Plesk preset. While individual account owners can set up MFA for their accounts, administrators may wish to enforce its use across all Plesk accounts for heightened security.
Enforcing MFA provides two primary scenarios: with or without the option for users to bypass the setup. In the strictest implementation, logging into Plesk without first configuring MFA will be entirely prevented, ensuring all users benefit from this enhanced security measure.
Important Note: It is crucial to understand that MFA enforcement, as described below, applies universally. There is currently no functionality to selectively enforce MFA for specific accounts or user types. Implementing these steps will enforce MFA for *all* Plesk accounts, including your administrator account.
Before enforcing MFA for all users, ensure you have successfully set up login to Plesk with verification codes for your own administrator account, following the detailed procedure outlined in the previous section.
Access and open the
panel.iniconfiguration file for editing. Its location varies based on your operating system:Plesk for Linux:
/usr/local/psa/admin/conf/panel.iniPlesk for Windows:
%plesk_dir%admin\conf\panel.ini
Alternatively, you can conveniently edit this file directly within the Plesk interface by utilizing the Panel.ini Editor extension.
Based on your desired enforcement strategy, add the appropriate lines to your
panel.inifile and then save the changes:-
To Enforce MFA Without Bypass Option:
This configuration mandates MFA setup for all users before they can access their Plesk accounts. Users without MFA configured will be presented with a message preventing them from proceeding until they complete the setup.
[ext-mfa] enforce = true allowSkipEnforce = falseUpon logging in without MFA configured, users will encounter a message similar to the one shown below, requiring them to set up MFA to continue using Plesk.
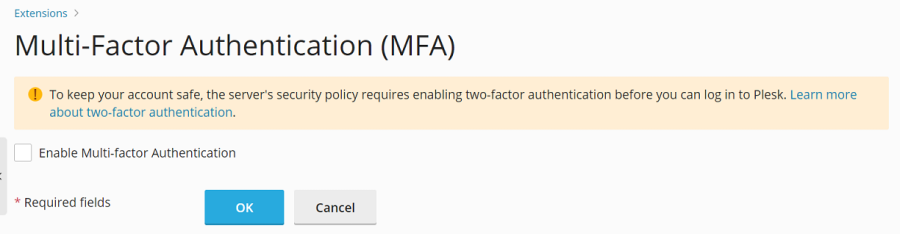
-
To Enforce MFA With Bypass Option:
This setting enforces MFA but provides users with an option to skip the setup. While they can access Plesk, they will continue to see the MFA prompt with every login until they configure it.
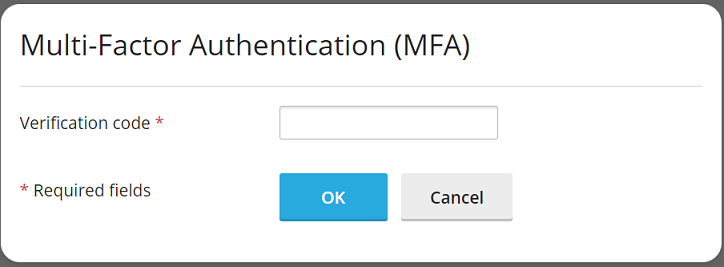
[ext-mfa] enforce = true allowSkipEnforce = trueUsers attempting to log in without MFA configured will see a message similar to this, offering the choice to skip the setup and proceed to Plesk, though the prompt will reappear with each subsequent login.
-
(Optional) Customizing the "Learn More" Link: After implementing MFA enforcement, users presented with the setup prompts (as illustrated in the screenshots above) will typically see a link directing them to a Plesk Knowledge Base article. This article provides comprehensive information on how MFA functions and its benefits for security.
If you prefer to direct your users to an alternative informational resource about MFA, you can customize this link. To do so, add the following lines to your
panel.inifile, replacing the example URL with your desired web page, and then save the file:[ext-mfa] learnMoreUrl = https://example.com ; Replace with the URL of your preferred informational web page




